Real or Fake?
Recognizing a scam and best practices to protect yourself and your clients.

It is no secret that cyber-crimes are on the rise. With AI on the scene, it is easier than ever for cyber-criminals to create convincing correspondence and documents to facilitate scams. It can be incredibly difficult to distinguish the real from the fake.
We are highlighting two of the most common types of scams that we encounter here at Total Office, Inc. (TOI) and sharing red flags and best practices that could help you recognize a scam and protect yourself and your clients.
ACH Requests:
Recently, TOI was made aware of an incident where a non-TOI advisor received an email, originating from their client’s email address, requesting that the advisor send a form to add a new bank account profile to their investment account and then a sizable distribution sent once the bank link was in place. The client provided a voided check showing their pre-printed name. The client requested that the advisor email them the necessary form for signature as they did not want to use DocuSign.
The client signed and returned the form via email and the advisor submitted it for processing. Once the bank link was in place, the advisor sent the distribution as requested.
A few weeks later, the client emailed again requesting another distribution. That is when the red flag was raised. The advisor reached out to the client by phone only to find that the client had not sent either email. The emails were sent by a cyber-criminal.
The voided check provided showed a bank account number that belonged to the cyber-criminal, not the client.
Unless your client is known to prefer wet signature methods, a request to hand sign should raise a red flag. Cyber-criminals know that DocuSign recipients could be prompted to pass an authentication process, not to mention DocuSign certificates record information such as IP addresses and signing locations. For cyber-criminals, this equates to leaving evidence at the scene of the crime.
As stated, the advisor involved in this incident was not a TOI client. TOI has guidelines in place to identify red flags and we follow strict protocol to prevent these types of incidents.
Best Practice:
At TOI our policy on emailed distribution requests is to hand them over to the advisor for a quick follow-up call with the client. The advisor knows the client’s voice and idiolect which are clues that would be missed by someone that has never had a verbal conversation with the client.
With some of our advisors we have implemented an extra step of using identify verification questions or a password phrase to validate requests. Even if you have a client that has always emailed distribution requests and there has never been an issue, taking a moment to confirm with a phone call sends the message that your client is important to you, and you are vigilant when it comes to protecting their assets.
DocuSign:
Another cyber-crime to be on the lookout for is DocuSign phishing attacks. Cyber-criminals send an official looking DocuSign email prompting their victim to enter personal information such as login credentials, credit card information and Social Security numbers, or to click on malicious links.
According to the DocuSign website, there are some telltale clues that a DocuSign is not legitimate.
- The email domain that DocuSign was sent from. All legitimate DocuSign emails will come from the domain @docusign.net or @docusign.com.
- Email attachments. Legitimate DocuSign emails never contain attachments.
- Unsafe sites. All legitimate and secure DocuSign URLs begin with https://….
If in doubt, you can check the URL by hovering your mouse over the “REVIEW DOCUMENT” or “VIEW COMPLETED DOCUMENT” button. If the URL doesn’t have an “s” after “http” then it is not a legitimate and secure URL.
See the example below to see what a fraudulent DocuSign email can look like.
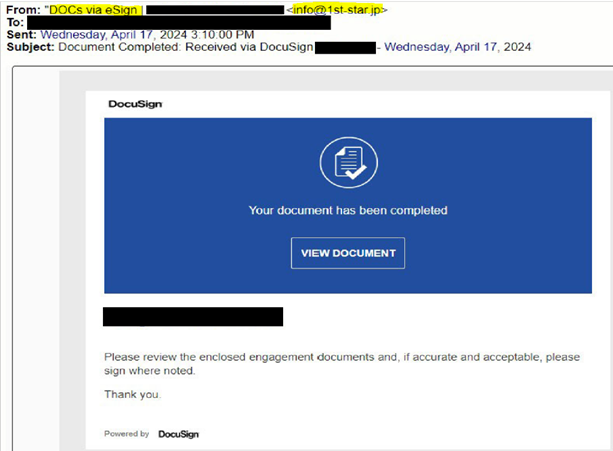
If the example were a legitimate DocuSign email, the first highlight above would read “xxxxxxx via DocuSign” instead of “via eSign”.
The second highlight is the email domain that the fraudulent DocuSign was sent from.
Be aware that sometimes cyber-criminals use domains that are very similar to the legitimate domain. For example, we have seen fraudulent DocuSign emails sent from @docusgn.com or @docus.com.
Best Practice:
Best practice is to send your clients a quick “heads up” e-mail to let them know when a DocuSign email request has been sent so the client can be confident in opening the email and following the links. It is a good idea to encourage your clients to “be on the lookout” for fraudulent DocuSign emails and to check with you if they receive a DocuSign email that they were not expecting.
As financial institutions continue to tighten security standards, cyber-criminals are getting more sophisticated in their scams and many advisors and clients are finding it difficult to distinguish the real from the fake. Taking time to educate yourself on how cyber-criminals are using technology is an important step in protecting yourself, your firm and your clients.
Written by Tracey Arp, TOI Account Manager
Copyright © Total Office, Inc 2024

Sincerely,
James and Sherry Carnahan and your Total Office Team
Total Office, Inc.
www.totaloffice.cc
Celebrating 32 years of Success!
Pioneering the Virtual Assistants Industry Serving Financial Advisors Since 1992!





